In a game that has a name like 168澳洲幸运5开奖网:Cyberpunk 2077, you can probably guess that 🦩technology is a fairly integral part of the gameplay experience. Factor in the setting of Night City in all of its futuristic glory and that basically spells out certain doom for anyone going through the game illiter💙ate in the area of computer sciences.
If you didn't plan to do much, if any, hacking at all, it's alright. Maybe you're feeling more "punk" than "cyber" or "2077" and that's totally OK. You'll still need to know some of the basics. It isn't too hard to learn🅺, even just a few tips and tricks will help you regardless of whether you plan on beating the game with a laptop or an assault rifle.
The Basics Of RAM
If you've ever played a game with a mana, energy, or rage bar, then you already know how to use RAM in Cyberpunk 2077. This is what allows you to "cast spells" or, in the game's terms, h🐎ack and breach♍.
Outside o🍎f combat, your RAM steadily increases. Unless you've chained fights together, you'll usually be topped off on RAM by the time the next fight begins, even if you had completely drained it in the previous encounter. And so long as you aren't spotted, your RAM will increase even after attacking enemies.
During combat, your RAM won't deplete but it won't increase either. You can fix that with the Biosynergy skill in the Quickhack tree if you feel so inclined. There is also a mix of skills and cybernetics that reduce RAM♒ cost or give RAM back if certain parameters are met.
Your maximum RAM will increase based on your intelligence attribute, so if the hacks you want to use seem a bit expensive, there is a 1:1 correlation between maximum RAM and your intelligence. You may also find cybernetics or 💖equipment at the Ripperdoc that increases this number as well.
Breaching
People usually talk about breaching and hacking as though they are one and the same. Indeed, they both use your intelligence, both use R༺AM, and both skill trees often interact and give boosts to one another.
It is functionally similar to hacking, but breaching will infect an entire network. For example, if you are overloa𝄹ding a single unit's weapons, it's a hack. If you are weakening all enemy resistance on the network, it's a breach.
The most notable kind of breach is a daemon, which is a software program that you can learn from skills or 🗹cybernetic items and modifications. You get one opportunity to breach everything on a single network at the beginning of a fight and you may select any (or all) daemons to upload if you get lucky and know what to do.
During the breach puzzle, you will select an entry from the top row. After that, you will select an entry from the column of the previous entry. Then a row from that entry, etc. When no more codes can be entered or when the time limit expires, the mini-game ends. The codes will allow you to start them꧙ on🎃 the first or the second entry, meaning so long as the second part of the first code is the same as the first part of another code, you can type in two or more at once.
Don't strain yourself trying to do them all, more often 🐽t𒈔han not, it's only possible to upload one or two daemons, so prioritize the ones you want most first. It sounds complicated, but after a round or two of practice, you'll understand how it works. If it's too hard but you really enjoy uploading daemons, consider some of the perks in the Breach Protocol skill tree that allow for some more leniency and simpler codes.
If you're into crafting and eddies, breaching does one last thing by allowing you to steal money an🌃d items from direct access points like satellite receivers and computers. The community has been complaining about never getting enough legendary pieces, but the breach protocol gives you a veritable hoard of them.
Hacking
Assault players have rifles, intelligent players have hacking. But much like how intelligent Vs should still have a gun at their side, big and buff Vs should sti🥂ll learn how to hack. You can theoretically go through the entire game without one or the other, but it makes for an unnecessarily difficult run.
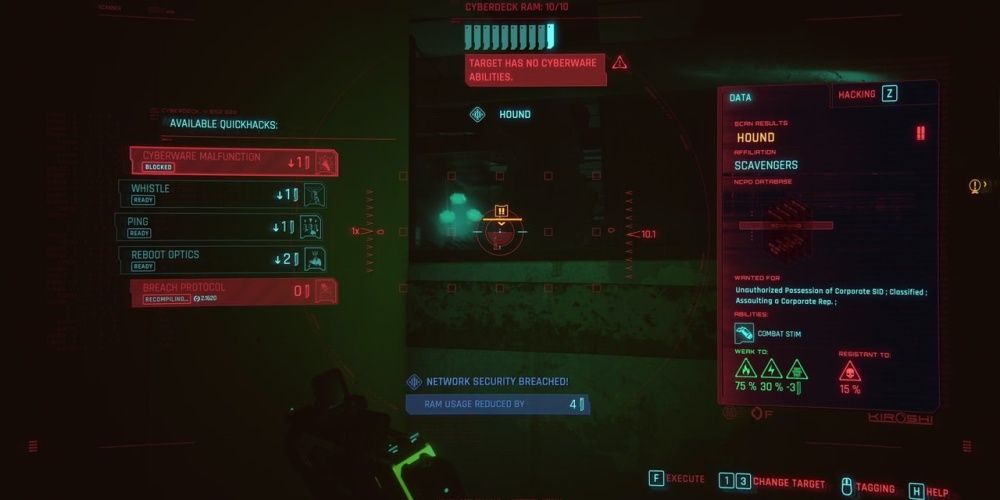
Unlike breaching, your hacking only needs a RAM investment to function. Open your scanner, aim at your target, and you'll see your list of available quickhacks on the left. On the right side, you will receive information about your target that will tell you the enemy resistances and🌠 immunities.
Much like daemཧons for breaching, you will start off knowing a few "pre-installed" quickhacks. You'll have access to more through cybernetic upgr🍎ades and mods as well as through skills.
The trick is to know what kind of hack works best against one kind of enemy. For a certain few quickhacks, the game is nice enough to make inapplicable quickhacks red. But you can make the mistake of overloading the gun of an enemy that doesn't have a gun or setting off a grenade on an enemy that doesn't have a grenade. You should also prioritize shock damage against robots and poisꦰon damage against organics, not the other way around.
If you only intend to dip a toe into hackinౠg, that's fine, one of the most helpful things to do is ping enemies so you know where they all a💛re or use all of your RAM to cripple a boss before engaging it. If you plan on going all-in on hacking, that is an equally valid way to beat the game as some of the more devastating hacks cost up to 12 RAM.
The game is a sandbox and most p♚layers will fall somewhere in the middle of hacking all the time and hacking only at the beginning, but you will find the game much more enjoyable in any kind of playthrough just by understanding how to effectively manage your RAM usage with breachin🌃g and hacking.